
Why it matters: LockBit is a “ransomware-as-a-service” operation where the malware creators and operators manage the backend, while affiliated “partners” breach victims’ networks. Sometimes, this chain of operations can lead to a clash between parties – especially when the affiliates go against the ransomware’s formal business policy.
It’s been a busy end of year for LockBit, the ransomware that is infamous providing its encryption abilities to script kids as well as other interested lovers in criminal activity. The ransomware was initially in charge of an assault against the* that is( of Lisbon Administration, which manages Portugal’s third-largest port and one of the most accessed ports in Europe.
The Port of Lisbon was targeted by LockBit on December 25, but according to the port’s administration, no operational activity was compromised. All the security measures designed as a response to this type of occurrence were quickly activated, the organization said, while it was working with the competent authorities to restore the affected systems.
As a matter of fact, the* that is( of Lisbon’s authoritative internet site continues to be traditional, and LockBit has posted a ransom note on the formal website in the Tor darknet. The cyber-criminals tend to be seeking a price that is hefty$1,500,000) to be paid by January 18, 2023, otherwise they will publish all the data they were able to steal from the port’s servers.
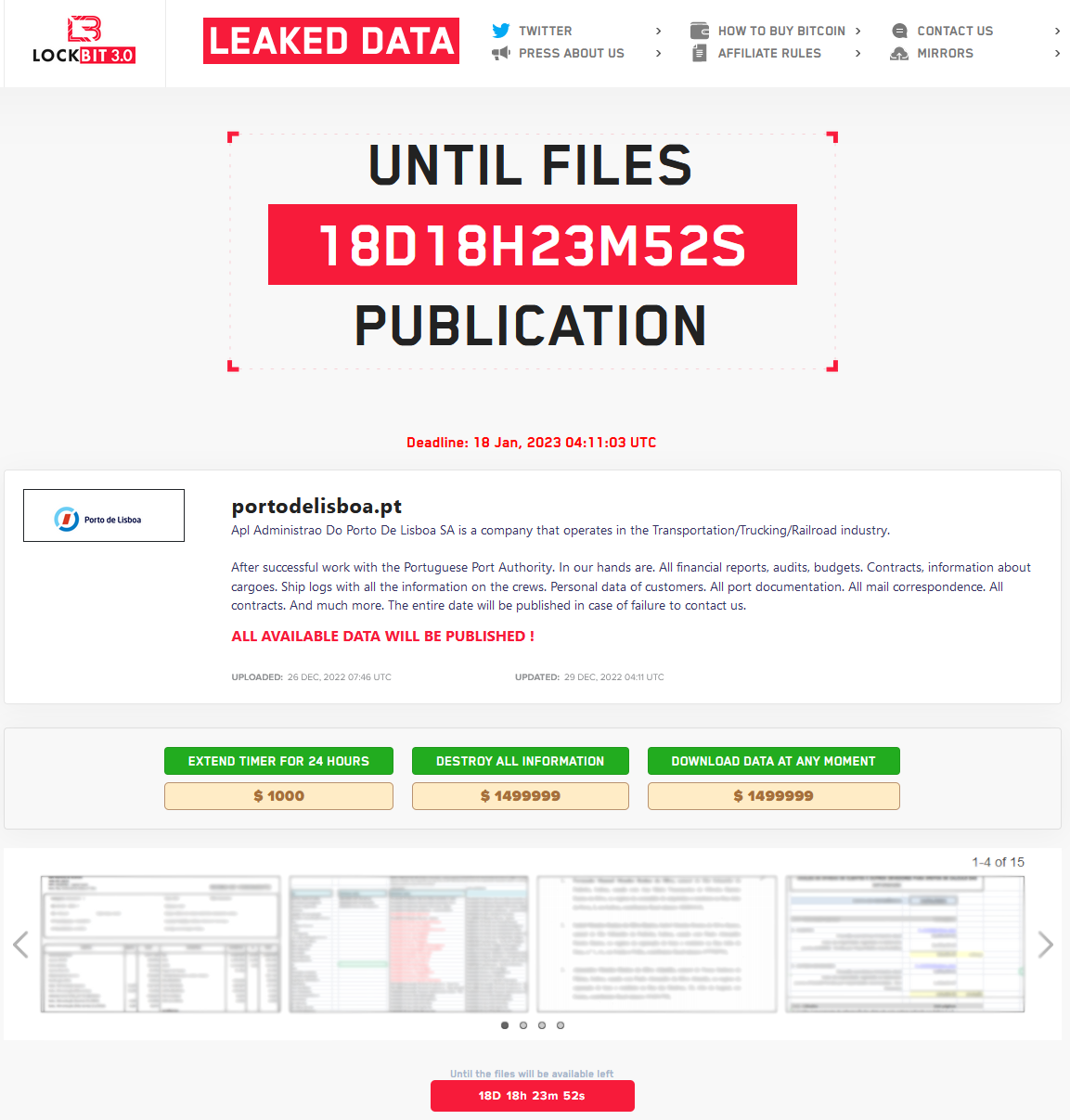
The LockBit gang says they got their hands on financial reports, audits, budgets, contracts, cargo information, ship logs, documentation, email messages and other business that is valuable private information. That’s completely good to encrypt, take and offer to interested events, because Port of Lisbon is not any youngsters’ medical center such as the 2nd victim that is outstanding collected at the end of 2022.
On December 18, one of LockBit’s affiliates attacked the Hospital for Sick Children (SickKids), a Canadian teaching hospital devoted to child healthcare. The attack impacted internal and systems that are corporate phone outlines, additionally the medical center internet site. While only “a few” systems were compromised, patients needed to handle delays in exam results and longer delay times.
According up to a update that is later the SickKids team was able to restore almost 50% of the hospital’s priority systems while others were still in progress. However, on new year’s eve, the LockBit gang posted a note to “formally apologize” for the attack against the* that is( medical center. “The partner whom attacked this hospital violated our principles, is obstructed and it is no further inside our affiliate marketer program,” the cyber-criminals said.
LockBit gave SickKids a decryptor that is free restore the encrypted data, even though the hospital was already in the process of restoring all the systems by itself. According to LockBit’s policy, affiliates of the ransomware operation have no permission to attack medical institutions to avoid deaths that are accidental. Stealing information is however permitted, nevertheless.


