Why it issues: A working joke within the safety neighborhood is that Intel CPUs have extra vulnerabilities than Swiss cheese, and new analysis launched this month hasn’t helped the corporate shake that popularity. A newly found side-channel assault is much less efficient towards Chipzilla’s latest CPUs, nevertheless it’s a reminder that speculative execution flaws are laborious to repair.
Researchers on the University of Maryland, Tsinghua University, and Beijing University of Posts and Telecommunications lately printed an attention-grabbing paper detailing a brand new side-channel assault on Intel processors that’s distinct from different vulnerabilities which have been uncovered prior to now.
This new flaw will be exploited as a aspect channel of Meltdown, leading to a 100% success fee towards processors reminiscent of Core i7-6700, Core i7-7700 and Core i9-10980XE. For these unfamiliar with Meltdown, it is a household of exploits that focus on a vital vulnerability in the way in which fashionable processors execute what’s often called “speculative execution,” to realize modest efficiency positive aspects in some instances.
While Meltdown has been mitigated on the working system, firmware, and {hardware} ranges, the issue has been troublesome to totally repair and thus persists to today. In the case of this new side-channel assault, it doesn’t depend on the caching system, and the setting doesn’t require resetting the EFLAGS register, so the researchers imagine it is going to be harder to mitigate.
The EFLAGS register is used to explain the present state of CPU operation, with a number of flags set to 1 or 0. The researchers discovered that they might benefit from the way in which it really works in Intel CPUs, the place a change within the EFLAGS register throughout transient execution could make sure “soar from conditional code” (Jcc) directions execute barely slower.
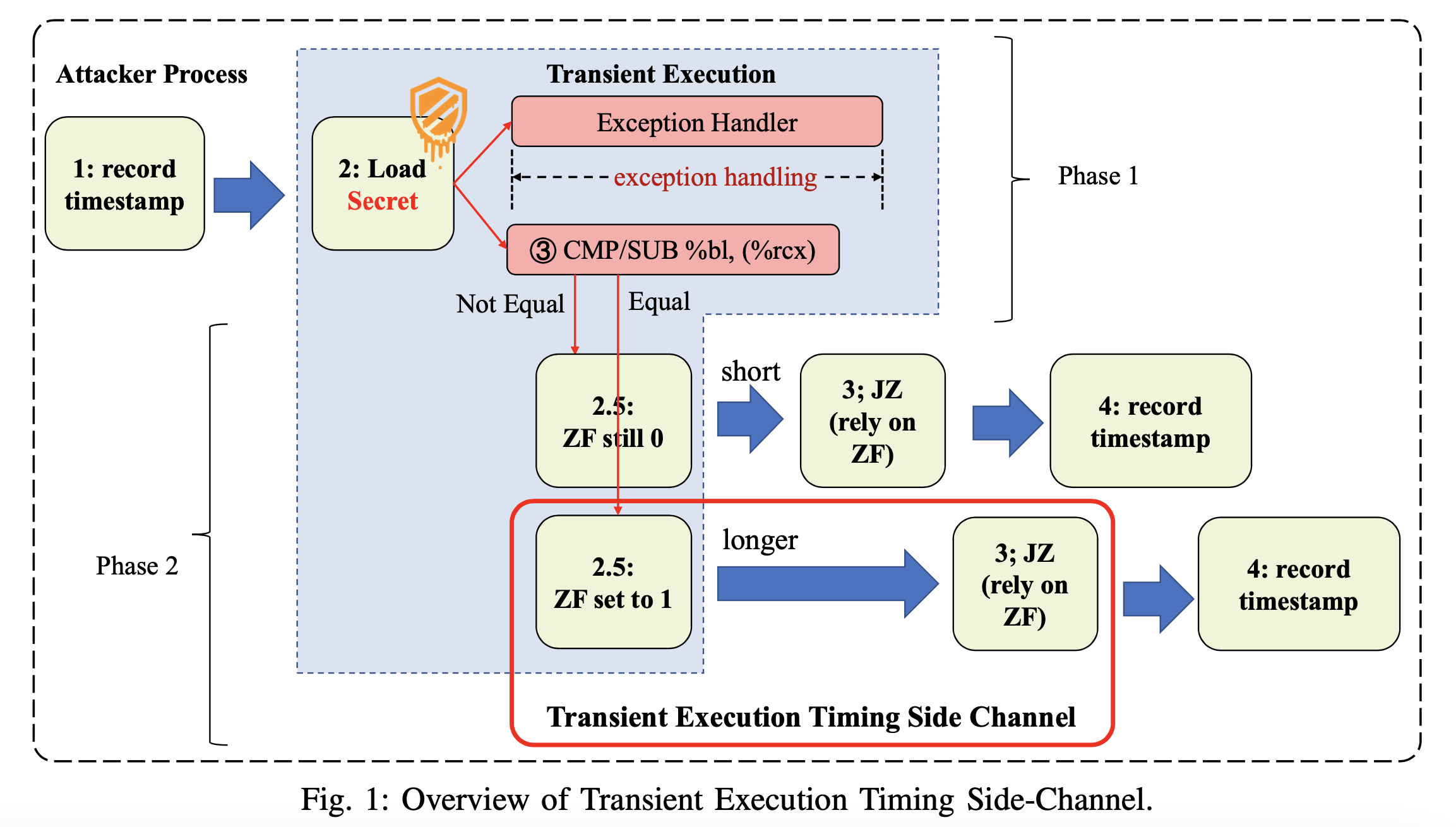
First, they encoded secret knowledge into the EFLAGS register, then measured the execution time of the Jcc instruction context to decode mentioned knowledge. The root explanation for the bug stays a thriller, however the researchers suspect that Intel makes use of a buffer within the execution items of its CPUs that takes time to get better when execution must be aborted, which in flip may result in Pause on the goal of mentioned buffer.
The excellent news is that this assault is barely much less efficient on newer chips (Intel eleventh era and later), and hackers have to repeat it hundreds of instances to realize the identical impact. Additionally, Intel’s new thirteenth Gen vPro processors function further safety administration options that present organizations with higher prevention and detection capabilities to defend towards side-channel assaults.
In their paper, the researchers present that their transient execution timing assaults will be mitigated, however they aren’t simple to implement as a result of they require vital adjustments to how the Jcc instruction works and meeting code optimizations.
Image credit score: Daniel Pantu


