
[ad_1]
Why it issues: Three vulnerabilities have been lately found affecting uninterruptable energy provides (UPS) made by APC. The vulnerability, labeled as crucial and excessive severity, is said to APC’s SMT, SMC, SCL, SMX, SRT, and SMTL product traces. The TLS-based assaults can lead to impacts starting from bodily injury of the gadget itself to unauthorized entry to a goal’s inside networks.
Device safety agency Armis found the APC vulnerabilities. The assault vectors, collectively named TLStorm, present hackers with the means to execute distant manipulation of the UPS. These gadgets provide backup energy for crucial gadgets and companies in information facilities, hospitals, and different organizations requiring uninterrupted backup energy.
Malicious actors exploiting the vulnerability can carry out distant code execution (RCE) assaults towards any weak APC Smart-UPS gadget. Such assaults allow unauthorized customers to change the UPS’s operation, doubtlessly damaging the facility provide itself or any belongings linked to it. Hackers can execute the assault with no person interplay and depart no hint of a breach.
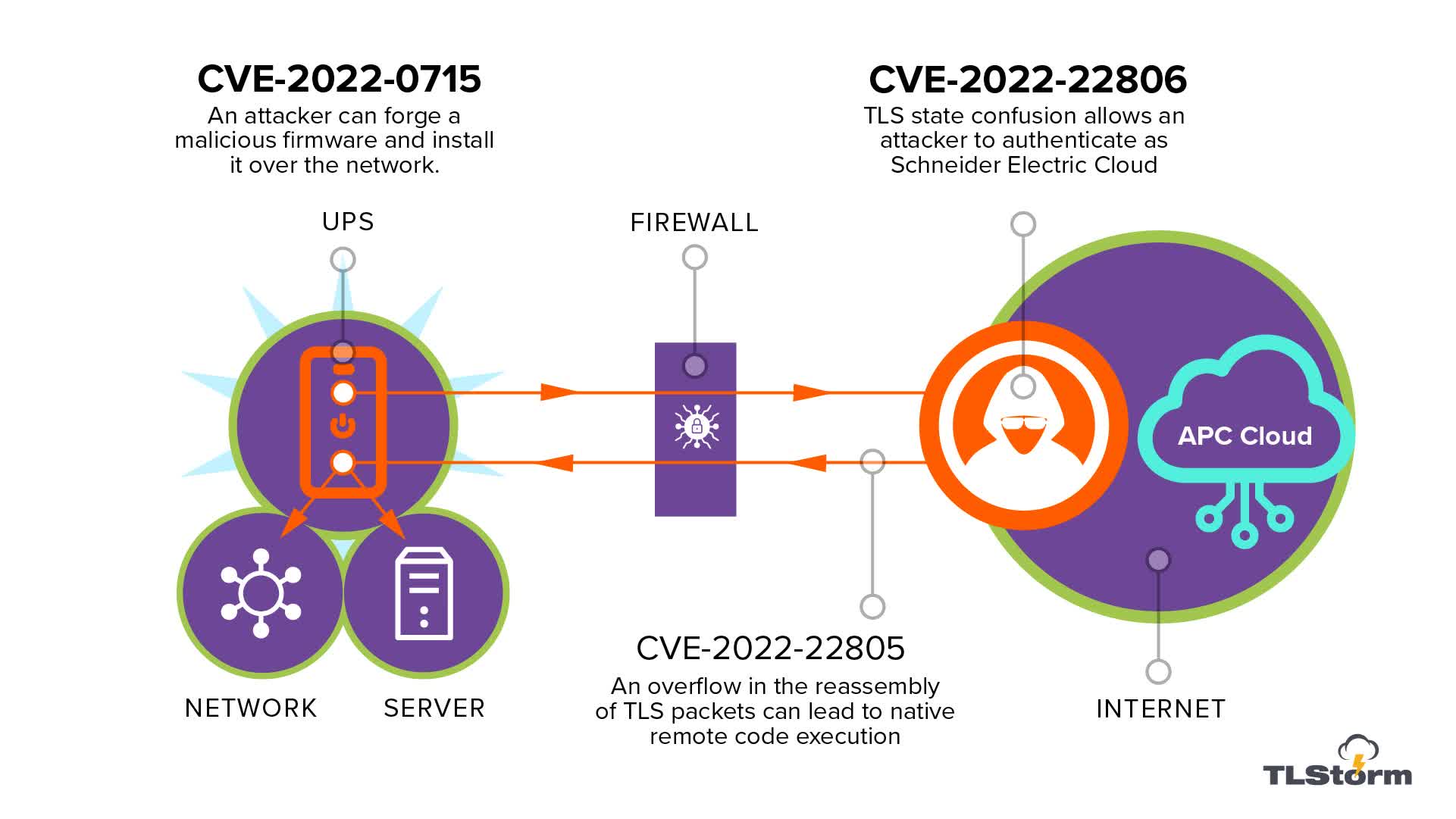
American Power Conversion’s Smart-UPS gadgets use a cloud connection for all configuration and management. This distant connectivity is the premise for 2 of TLStorm’s three vulnerabilities. The third is said to a design flaw stopping firmware updates from receiving safe cryptographic signatures.
- CVE-2022-22806 – TLS authentication bypass: a state confusion within the TLS handshake results in authentication bypass, resulting in distant code execution (RCE) utilizing a community firmware improve
- CVE-2022-22805 – TLS buffer overflow: a reminiscence corruption bug in packet reassembly (RCE)
- CVE-2022-0715 – Unsigned firmware improve that may be up to date over the community (RCE)
Armis researchers estimate that eight out of ten corporations utilizing the gadgets are at present weak to TLStorm-based assaults. Mitigation measures embody altering the default NMC password (“apc”), putting in a publicly signed SSL certificates, deploying entry management lists, and putting in the patches discovered on the Schneider Electric web site.
[ad_2]


