[ad_1]
Why it issues: As ransomware stays a prevalent safety menace, a vital step in countering attackers is figuring out their strategies. Security researchers discovered that a number of of probably the most prolific teams share a big proportion of their ways, doubtlessly making them extra predictable.
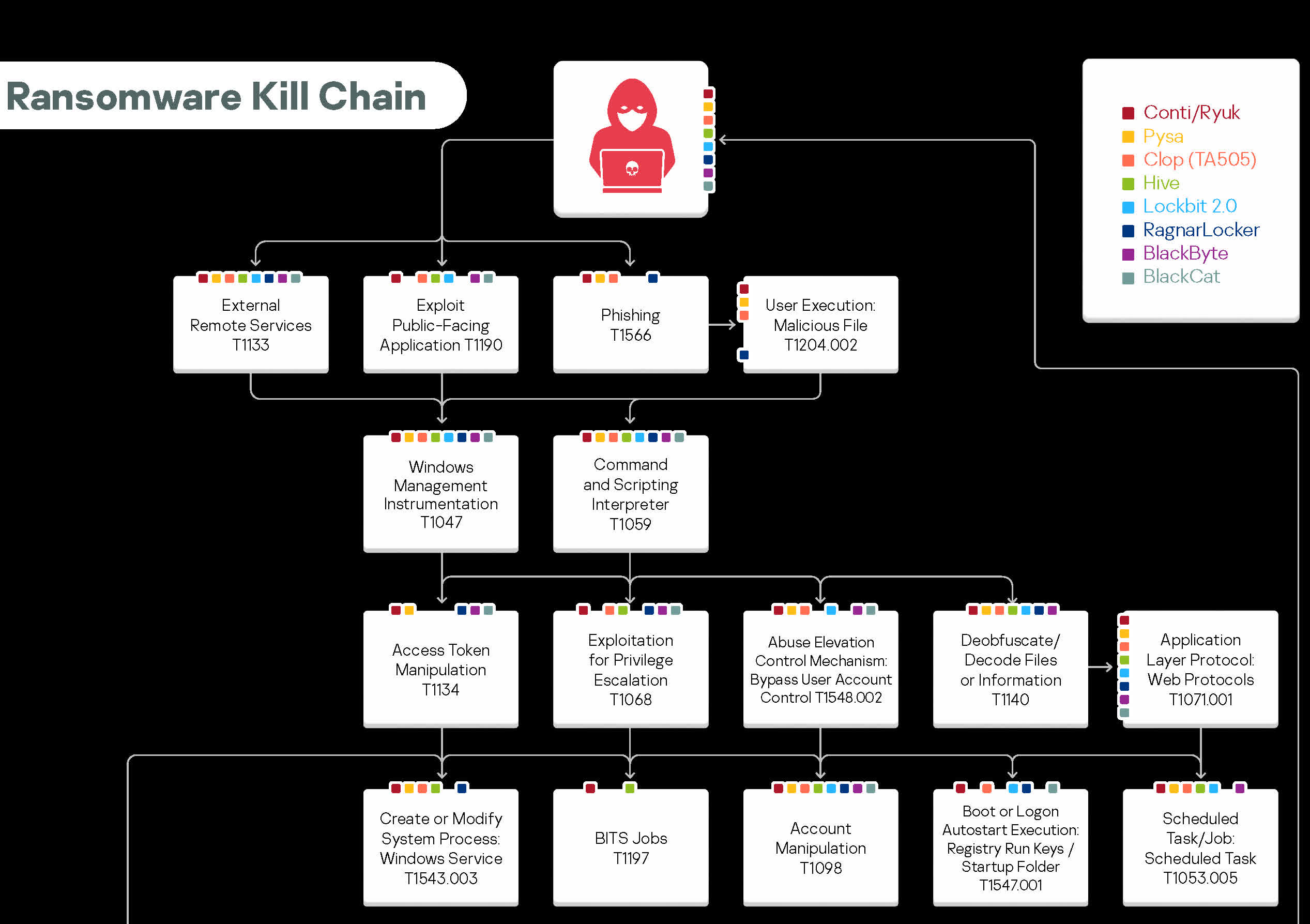
A brand new report from safety firm Kaspersky reveals that eight of probably the most lively ransomware gangs function with very related patterns. Analysis, digital forensics specialists, and different safety staff may use these similarities to establish and struggle these attackers extra effectively.
The report analyzes the ways, strategies, and procedures of (TTP) of the ransomware teams Conti/Ryuk, Pysa, Clop (TA505), Hive, Lockbit 2.0, RagnarLocker, BlackByte, and BlackCat. VentureBeat notes that these eight gangs have attacked over 500 organizations in varied industries within the US, the UK, and Germany within the final yr. Kaspersky constructed an fascinating chart itemizing dozens of steps in ransomware assaults and indicating which attackers bear every step. None of them are distinctive to 1 group.
For occasion, all of the teams like to start out by attacking exterior distant companies, whereas solely half additionally open with phishing. All the gangs are inclined to favor targets like Windows Management Instrumentation, command and scripting interpreters, software layer protocols, net protocols, signed binary execution, and others.
Common steps like stopping system restoration or encrypting probably the most impactful knowledge appear apparent. However, among the least prevalent ways contain BITS jobs, lifting account credentials from password shops, or getting them from net browsers.
Early in June, a Foxconn facility in Mexico suffered an assault from Lockbit 2.0. Other latest ransomware victims embrace QNAP, Asustor, and Nvidia.
[ad_2]