[ad_1]
What simply occurred? Earlier this week, Cloudflare engineers recognized one of many largest distributed denial-of-service (DDOS) assaults ever tried. The assault, made in opposition to an unidentified cryptocurrency platform, was recognized and mitigated in below 20 seconds. The people behind the act flooded the community with greater than 15 million requests.
In addition to the assault’s dimension, using HTTPS fairly than typical HTTP requests additional difficult the difficulty—the safe protocol ends in extra useful resource overhead because of the compute-intensive nature of the safe HTTPS request. According to Cloudflare, the botnet liable for finishing up the assault represented 6,000 bots from 112 international locations world wide.

The assault is believed to have leveraged servers from internet hosting suppliers working weak Java-based functions. Those servers had been possible unpatched or not up to date and prone to CVE-2022-21449, Psychic Signatures in Java. The vulnerability permits attackers to make use of the elliptic curve digital signature algorithm (ECDSA) to forge SSL certificates and different authentication-based info in an effort to acquire undesirable entry.
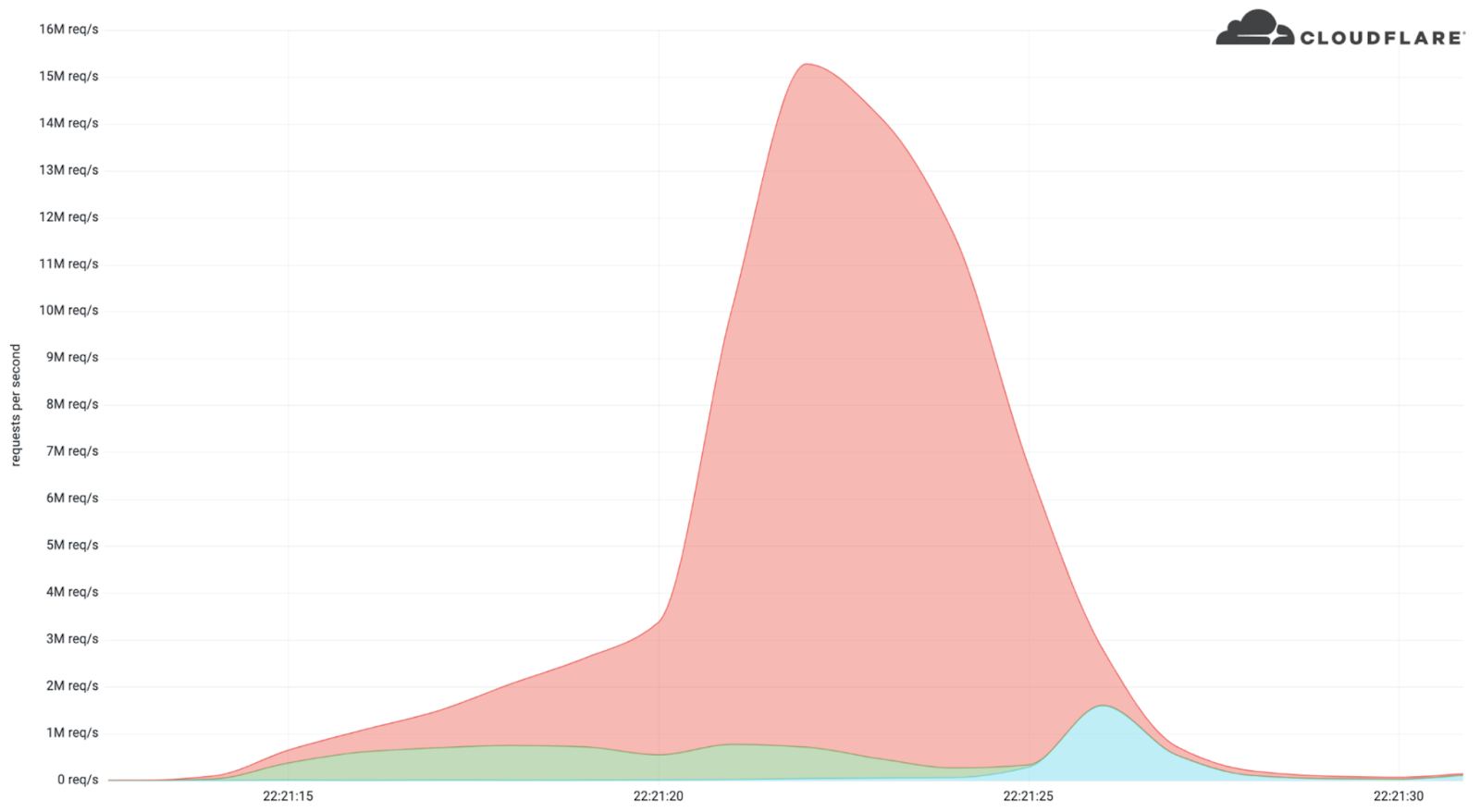
The sharp spike in Cloudflare’s site visitors analytics reveals simply how rapidly the assault was capable of ramp up. At 22:21:15 the platform recorded between 500,000 and 1 million requests. Within 5 seconds, that quantity grew to virtually 3 million requests. At this level the assault’s depth escalated, producing roughly 15.3 million requests throughout the subsequent 5 seconds. Several seconds later, Cloudflare was capable of mitigate the assault, bringing site visitors patterns again to anticipated ranges.
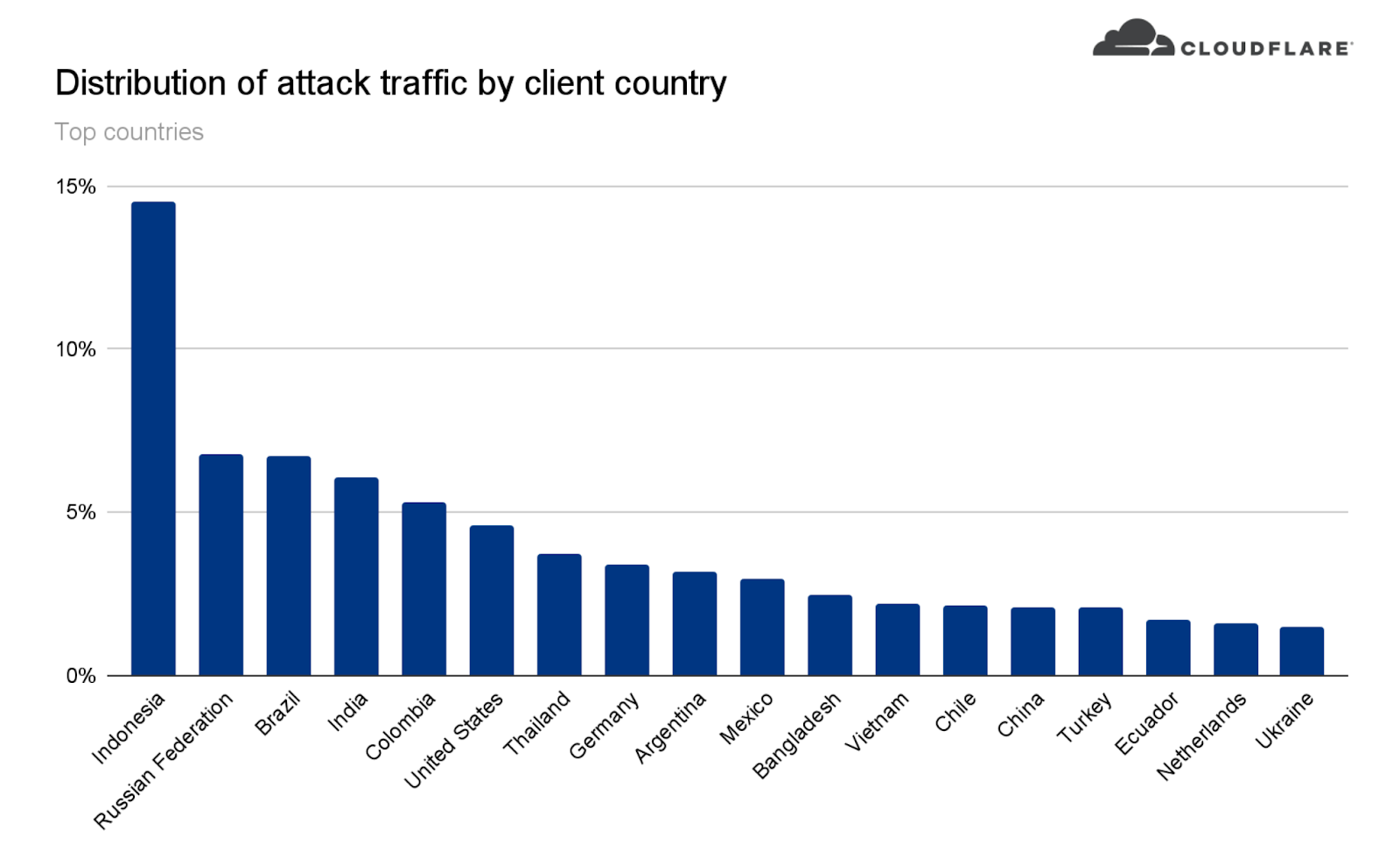
According to Cloudflare’s information, virtually 15% of the assaults originated in Indonesia. The Russian Federation, Brazil, India, Columbia, and United States every accounted for roughly 5% of the origination factors. Cloudflare engineers and safety specialists concluded that the assaults originated from greater than 1,300 completely different networks throughout the complete 112 international locations recognized. They had been additionally shocked to seek out that not like different assaults, many of those assaults originated from information facilities fairly than typical ISP-based residential networks.
Oracle has since launched a crucial patch replace advisory to assist customers mitigate any potential vulnerability. Administrators of probably weak programs ought to overview this info to make sure any Java-related dangers are minimized.
The dimension of the assault, in addition to the sources utilized and energy required to execute the HTTPS-based assault, are clear indicators that hackers are persevering with to strengthen their weapons in what appears to be a unending arms race. Staying up-to-date on the newest safety patches and proposals can assist to attenuate the potential for falling sufferer to those and comparable assaults sooner or later.
Image credit score: Traffic sample and placement breakdown from Cloudflare
[ad_2]


