
Cut corners: Past auto theft makes an attempt have concerned something from smashing home windows to relaying FOB code sequences. But a spate of injury to bumpers and headlights led the researchers to a brand new technique that depends on the automobile’s controller space community (CAN) and makes use of what seems to be nothing greater than a easy speaker to realize entry. Worse, it takes about two minutes from begin to end.
Sometimes criminals inadvertently select the fallacious targets when planning their crimes. In this case, automotive thieves took benefit of a brand new keyless entry and automotive theft tactic that occurred to be the Toyota SUV of a cybersecurity analyst who focuses on automotive safety. What he found was a method that went past easy smash-and-grab and extra subtle strategies of sign hijacking.
ian taberCVE-2023-29389, found by cybersecurity and automotive hacking consultants, signifies that Toyota RAV4 automobiles are in a position to robotically belief messages from different digital management items (ECUs). By pulling off the bumper to disclose the headlight connector, a thief can acquire entry to the CAN bus to ship faux key authentication messages. Once authenticated, the thief can begin the automotive and drive away with out a downside.
After finding out the info and communication conduct on the RAV4’s CAN bus, Tabor found that different ECUs have been malfunctioning concurrently the CAN bus error. This discovery prompted Tabor to conduct extra analysis by way of YouTube, the darkish net and different sources. Tabor’s analysis led to the acquisition and evaluation of an emergency begin system supposed for use by a property proprietor or locksmith within the occasion a key’s misplaced, stolen, or in any other case unavailable. Working with one other auto security knowledgeable, Ken Tindell, Tabor efficiently reverse-engineered the emergency begin system to see the way it communicated with Toyota’s CAN bus.
Although marketed as an emergency boot system, the product Tabor purchased and used was designed to seem like a easy JBL moveable speaker. According to Tindell, the faux play button on the speaker housing is wired right into a PIC18F chip. When pressed, a CAN message burst instructs the door ECU to unlock the doorways. Once unlocked, the thief would disengage the CAN injector, acquire entry to the automotive, and drive away. Full particulars of the system, the way it works, and the way simple (and value) it’s to construct can be found on the Canis Automotive Labs web site.
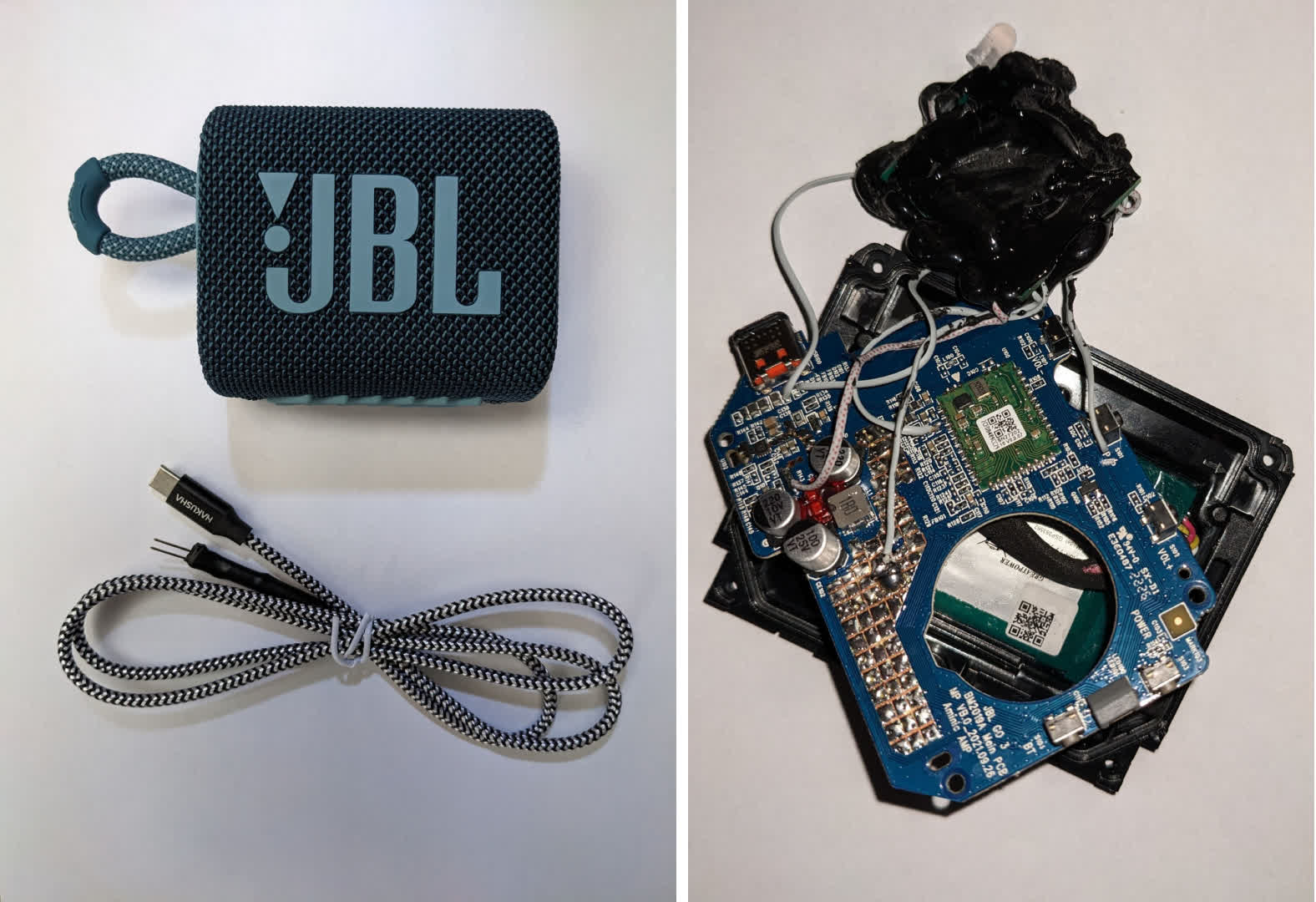
While the assault was efficiently replicated on the Toyota RAV4, there may be motive to imagine that related assaults could happen on different automobiles utilizing the identical know-how and structure. Tabor and Tindell have alerted Toyota to this vulnerability within the hope that will probably be hardened and not exploited. Unfortunately, they’ve but to obtain any affirmation or response.


